Indonesia Data Privacy
Overview
Indonesia enacted its Personal Data Protection Law (Law of the Republic of Indonesia Number 27 Year 2022) (PDP Law) on October 17, 2022. The PDP Law applies to persons residing (i) in Indonesia; and (ii) outside Indonesia if their actions have legal consequences in Indonesia or for Indonesian data subjects abroad.
The PDP Law distinguishes between data controller and data processor, and applies different data handling obligations on each of them. A data controller is a person who determines the objectives of, and exercises control over, the processing of personal data. A data processor is a person who processes data at the instruction of a data controller. At a high level, some of the key obligations of data controllers include.:
- Processing personal data in accordance with the specified legal bases for processing, including consent from the data subject, contractual necessity and legitimate interest
- Implementing appropriate security measures to protect the personal data from unauthorized disclosure
- Responding to the rights of data subjects including rights to access and correct their personal data, and requests to delete their personal data
- Transferring personal data outside of Indonesia only where conditions for such transfer have been fulfilled
For data processors, the PDP Law requires their personal data processing to be only in accordance with the instructions of the data controller. The PDP Law does not include any data localization requirements.
Existing personal data protection regulations, including the Law No. 11 of 2008 regarding Electronic Information and Transactions, Government Regulation No. 71 of 2019 regarding Operation of Electronic System and Transactions (GR 71) (which amended Government Regulation No. 82 of 2012 Concerning Electronic System and Transaction Operation), and Minister of Communications & Informatics Regulation No. 20 of 2016 regarding the Protection of Personal Data in an Electronic System (Ministerial Regulation 20) continue to remain in force to the extent they do not conflict with the PDP Law.
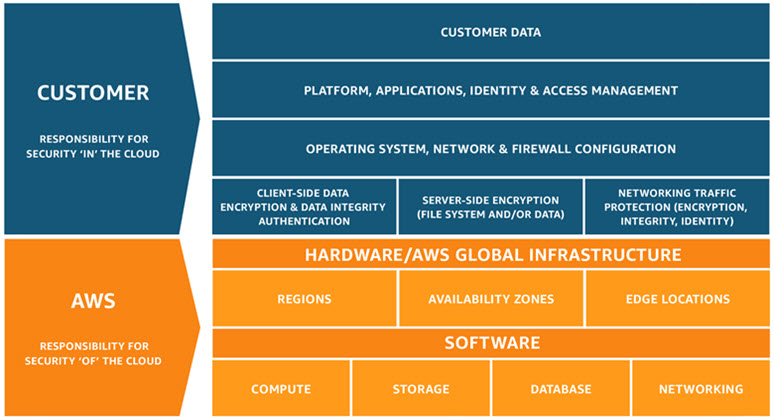
AWS is vigilant about your privacy and data security. Security at AWS starts with our core infrastructure. Custom-built for the cloud and designed to meet the most stringent security requirements in the world, our infrastructure is monitored 24x7 to ensure the confidentiality, integrity, and availability of our customer's data. The same world-class security experts who monitor this infrastructure also build and maintain our broad selection of innovative security services, which can help you simplify meeting your own security and regulatory requirements. As an AWS customer, regardless of your size or location, you inherit all the benefits of our experience, tested against the strictest of third-party assurance frameworks.
AWS implements and maintains technical and organizational security measures applicable to AWS cloud infrastructure services under globally recognized security assurance frameworks and certifications, including ISO 27001, ISO 27017, ISO 27018, ISO 27701, ISO 22301, PCI DSS Level 1, and SOC 1, 2 and 3. These technical and organizational security measures are validated by independent third-party assessors, and are designed to prevent unauthorized access to or disclosure of customer content.
For example, ISO 27018 is the first International code of practice that focuses on protection of personal data in the cloud. It is based on ISO information security standard 27002 and provides implementation guidance on ISO 27002 controls applicable to Personally Identifiable Information (PII) processed by public cloud service providers. This demonstrates to customers that AWS has a system of controls in place that specifically address the privacy protection of their content.
These comprehensive AWS technical and organizational measures are consistent with typical regulatory goals to protect personal data. Customers using AWS services maintain control over their content and are responsible for implementing additional security measures based on their specific needs, including content classification, encryption, access management and security credentials.
As AWS does not have visibility into or knowledge of what customers are uploading onto its network, including whether or not that data is deemed subject to the PDP Law, customers are ultimately responsible for their own compliance with the PDP Law and related regulations. The content on this page supplements the existing Data Privacy resources to help you align your requirements with the AWS Shared Responsibility Model when you store and process personal data using AWS services.
Protect your data
Earning customer trust is the foundation of our business at AWS and we know you trust us to protect your most critical and sensitive assets: your data. We earn this trust by working closely with you to understand your data protection needs, and by offering the most comprehensive set of services, tooling, and expertise to help you protect your data. To do this, we provide technical, operational, and contractual measures needed to protect your data. With AWS, you manage the privacy controls of your data, control how your data is used, who has access to it, and how it is encrypted. We underpin these capabilities with the most flexible and secure cloud computing environment available today.